No, its not actually a Drupal requirement. I guarantee you though that once your friends and relatives find out your hosting your own website they will ask you to host one for them eventually. We can't have granny hosting her silver surfers info site and having access to the entire server. Granny may want to upload a large amount of images and her site does not have a file manager so she wants to do it via FTP. This means we need to give her access AND secure it against accidental editing of important files. My preferred method for doing this is by creating an SFTP jail. This limits the user to viewing their home directory, as far as they are concerned that's all that exists and they'll never be able to damage any of the important files on the server.
First we are going to create a group to put granny in. This is because it will save us a bit of work if uncle Bill asks us to host his website too. To create the group we use this command
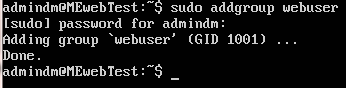
sudo addgroup webuser
The group name is not important but its a good idea to make it something meaningful, in this case "webuser" because its for all our ambitious web host family members.
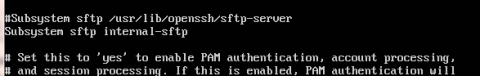
Next we need to configure OpenSSH to set up the jail. The jail restricts any user in the webuser group to their home directory. We need to edit OpenSSH's configuration file /etc/ssh/sshd_config.
sudo nano /etc/ssh/sshd_config
Look down the file until you find a line that starts with "Subsystem sftp". It's usually near the bottom of the file. Comment the line out by putting a # at the start of the line and on the next line put "Subsystem sftp internal-sftp".
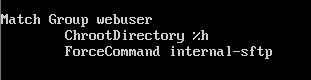
Next we need to add some extra code at the end of the configuration file to make the jail work. Add this at the very bottom of the file.
Match Group webuser
ChrootDirectory %h
ForceCommand internal-sftp
This applies the jail to any user we put in the webuser group. The %h means the users home directory. We could use /home/granny for this but if we ever change granny's home directory the jail would still lock her in the old directory. Now close the file and save the changes.
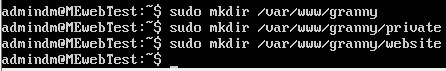
I'm going to put granny's home directory in /var/www/granny which is the default location apache uses for its web sites. I put it here to differentiate the account from a full server user (my own), but you can put the home directory anywhere you want. First we are going to create a few directories with the mkdir command.
sudo mkdir /var/www/granny
sudo mkdir /var/www/granny/private
sudo mkdir /var/www/granny/website
Our new user will be able to read and write either of these two folders but not in their home directory. This is due to the way we have to setup permissions to make the jail work. website will contain our Drupal installation and we will fill this later. private will remain empty, its just to give granny some storage space that isn't part of her website.
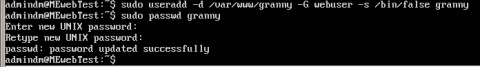
Now lets actually create the user for granny. We are going to create the user, add it to the webuser group, restrict shell access and set its home directory in 1 command. Use this
sudo useradd -d /var/www/granny -G webuser -s /bin/false granny
You can create a user with "sudo useradd username". This will create a user with default settings. -d is the option to set the home directory, otherwise it would be set as /home/username. -G sets the user group, this is only needed as we are using the group as our match for the SSH jail. -s is to setup a dummy shell so granny can't access the server terminal. Notice we have not set a password, we do this with
sudo passwd granny
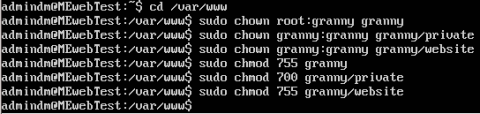
In order for the jail to work the users home directory needs to be owned by the servers root account. We also need to make sure the directories underneath it are owned by granny and writable by her. Run these commands.
cd /var/www
sudo chown root:granny granny
sudo chown granny:granny granny/private
sudo chown granny:granny granny/website
sudo chmod 755 granny
sudo chmod 700 granny/private
sudo chmod 755 granny/website
The cd command changes the current directory to /var/www to save us some typing. chown sets the owner of the folder "granny" to root and the owner of its subfolders to granny. chmod sets the permissions for the folders. The 3 numbers set the permissions for the owner, group and public. 7 gives read, write and execute access. 5 gives read and execute access. 0 gives no access. In this case we are giving the owner of all 3 folders read, write and execute access. For the private folder we set the group and public access to 0, this means only granny will be able to see the files in this folder. For the website folder we set group and public access to read and execute. There wouldn't be much point having a website that only the user who owns it could access.
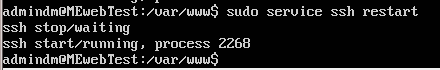
All that's left now is to restart the SSH daemon. To do this
sudo service ssh restart
Now when you log into the server as granny she will only be able to see 2 folders.